The Peak of the Pyramid: Attack Disruption
In our last blog we investigated why traditional SOC methods are too slow and what good should look like through Attack Disruption. In this blog we are going to delve more into why Attack Disruption is so effective by making you a harder target.
If you missed the last blog check that out here.
The Pyramid of Pain
This is a diagram we’re sure you’ve come across, The Pyramid of Pain.
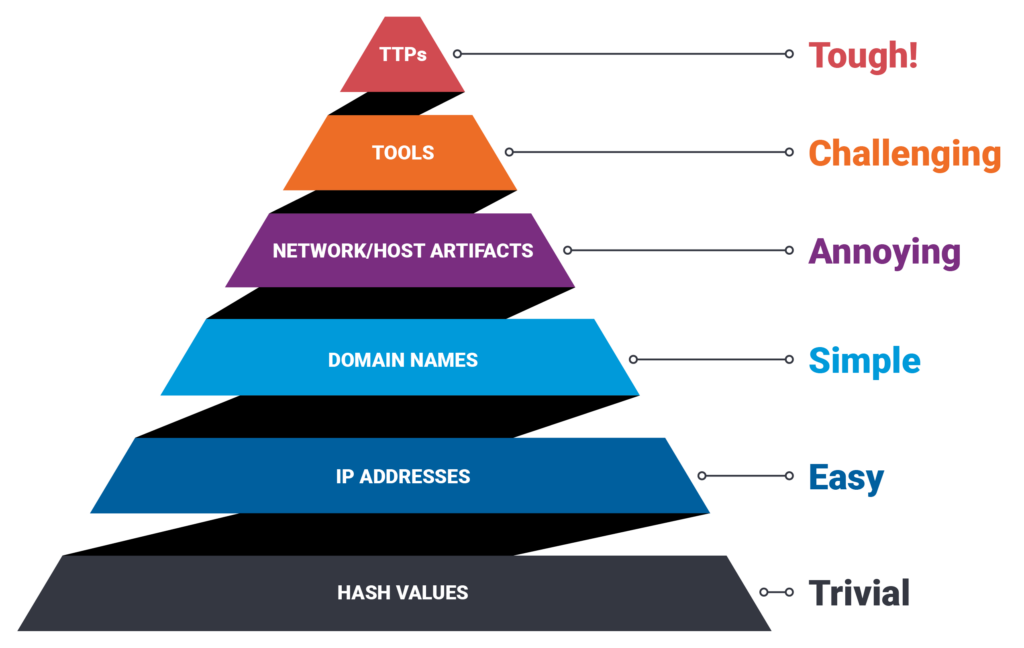
The Pyramid of Pain is a conceptual model showcasing the different levels of difficulty and expense that an attacker might face when trying to avoid being detected and sustaining their attack in the realm of cybersecurity defences.
This pyramid arrangement classifies various indicators and characteristics associated with cyber threats. At the base are the simpler and less costly elements to alter, such as hash values, IP addresses, and domain names. As you move up the pyramid, you encounter more intricate and expensive aspects to change, such as Tactics, Techniques, and Procedures (TTPs), as outlined in the MITRE ATT&CK framework.
Utilising Attack Disruption puts your cyber security operations at the peak of this pyramid. Making the time and monitory effort required by a threat actor to go undetected in your environment much higher and as a result making your business a much less desirable target.
But this diagram predominantly focusses on detection indicator which are just one of many components that form part of an effective Threat Detection & Response operation. So, what are the other core components and does this model apply to them?
Threat Detection & Disruption Maturity Model
What we have created here is a Threat Detection & Attack Disruption maturity model.
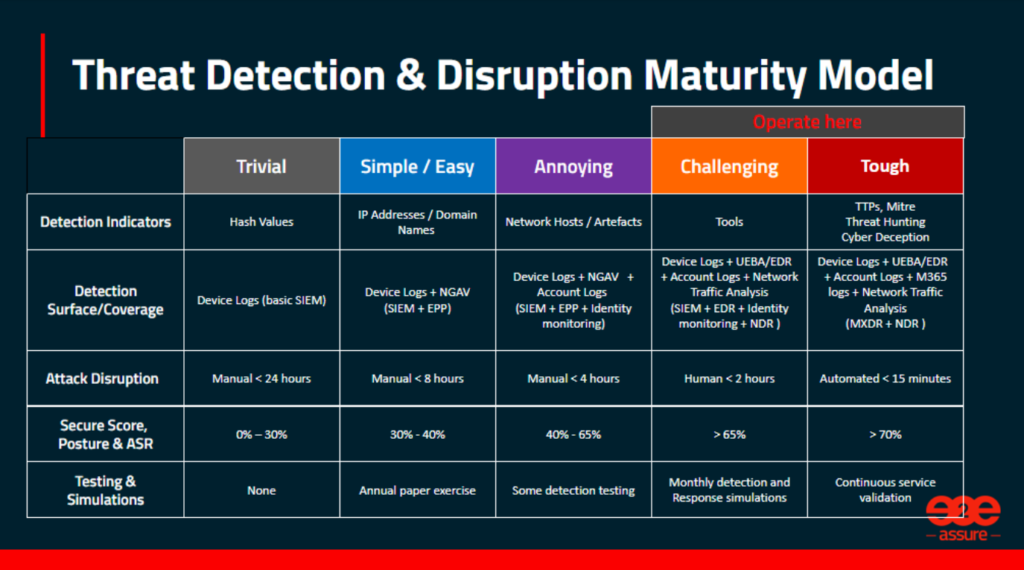
As you can see, we have taken the Trivial to Tough rankings from the pyramid of pain, which are the column headings. Additionally, there are four other areas, on top of detection indicators, that we can use to assess how hard of a target a business is to a threat actor:
- Detection Surface/Coverage: The reach of IT assets upon which we can detect attacker activity.
It’s important to recognise that sophisticated detection indicators will not be as effective if only deployed to a small proportion of your total attack surface, hence the next row applies the same ranking to the breadth, scale and sophistication of log analysis. Ranging from basic device log aggregation to full-on correlated behavioural analytics, traffic analysis and cyber deception.
- Attack Disruption: The measure of how quickly an attack can be contained.
At the challenging and tough end of this scale this relies on how assertively the built in automation capabilities of the more sophisticated SOC tools are activated.
- Secure Score, posture & ASR: The indicator of our strong your company cyber posture and hygiene is.
For those organisations that have Microsoft365 defender, Secure Score is a simple means to get a view on how well hardened the configuration of your environment is. Other posture maturity models and attack surface reduction scoring methodologies are available. To be a challenging target you want to be aiming at an equivalent Secure Score of greater than 65%
- Testing & Simulations: How regularly a company tests the effectiveness of their current cyber operations.
The final row in this table is Testing & Simulations, this is crucial to being able to answer the question of how quickly can you detect and disrupt attacker activity.
Without validating that your detection rules will fire when expected and measuring how long it takes to contain threats, you can’t be sure that your initial SOC implementation is still functioning as expected.
Attackers evolve their tactics, infrastructures expand and contract, users change roles and move data. So, this needs to be a regular activity to ensure operational effectiveness.
As the model suggests, all businesses should be operating in the Challenging and Tough columns, and this is where Attack Disruption allows you to operate.
Make your business a poor investment for cyber criminals
To sum it up, most threat actors are also running a business. They want the highest return on their investment possible, therefore they will focus their efforts on the easy wins. The businesses operating in the Trivial to Annoying columns will be the first on their target list.
Get your business off this list by operating in the Challenging to Tough columns, make it harder for threat actors to create a good business case for coming after you and utilise Attack Disruption techniques in your cyber security operations to do so.
If your interest has been piqued in how e2e-assure can help you mature your cyber security defences and take your cyber maturity to the next level through Attack Disruption, contact our team.
They will be happy to give you more information about our services as well as organising a demo for you to see first-hand Attack Disruption in action.
