Attack Disruption : The Cyber Defence Strategy for 2024
Attack disruption should be implemented into all modern SOCs. The e2e-assure industry report, Threat Detection 2024: Rejuvenating Cyber Defence Strategies, found that 59% of those outsourcing their SOC operation described their current provider as underperforming. Unfortunately, this isn’t surprising if we assess the traditional SOC methods that most providers are still using in 2024.
The ever-increasing sophistication, speed and frequency of cyber-attacks calls for faster response times to protect UK businesses. At e2e-assure, we refer to this modern approach to SOC operations as Attack Disruption.
In this blog we will cover:
- Traditional SOC operations and why these are too slow.
- What Attack Disruption is and why it is so necessary in 2024.
Traditional SOC Operations
How is the traditional SOC set up?
In a traditional SOC operation, the IT infrastructure is configured with a user endpoint device that connects to a network containing servers housing valuable data targeted by potential threat actors. The user endpoint device is equipped with a detection and response agent, yet notably, it operates exclusively in what we refer to as “audit mode.”
Events and alerts may be generated and sent to a central Security Incident and Event Management (SIEM) platform for logging, but if the alert is not tuned to the correct priority or is using an outdated ruleset, this won’t be enough to raise a critical incident.
What is the impact?
As a result, when hackers use their tactics, techniques and procedures (TTPs) to gain initial access, an alert might be generated but no containment action is triggered on the endpoint. Typically, these alerts might sit under a pile of higher priority alerts vying for burnout analysts’ attention.
This gives the threat actor plenty of time to jump off from the initial entry point and find areas of the infrastructure where it is easier to move around undetected.
When the attacker is ready to complete the campaign, they will look to setup communications to a remote control server in preparation for the final stages. These communications are relatively straightforward to detect, and it is often at this stage that traditional SOC tools will correlate the previous ‘lower level’ alerts with the more overt signals and raise a high priority incident for analyst triage.
It’s at this point that the SOC escalation chain kicks in and depending on the time of day, day of the week, or time of year, it may take several hours before approval is given by the named authority to take containment actions.
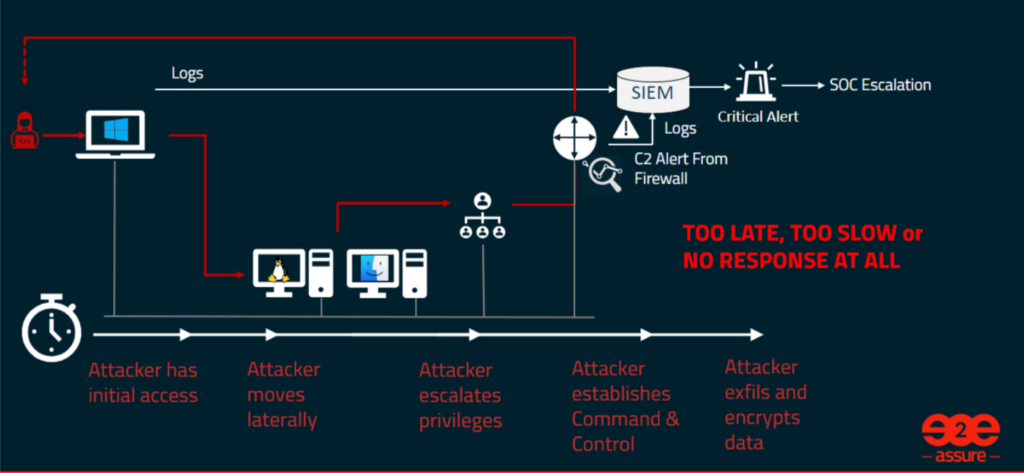
In this far too familiar scenario, attackers are moving much quicker from initial access to data encryption, meaning that attackers have already completed their objective before containment measures are activated.
So, what is the alternative approach?
Attack Disruption.
What is Attack Disruption?
In its simplest form Attack Disruption is; containing first and investigating immediately.
Attack Disruption is the way in which threat actors are automatically intercepted at the beginning of their attack to limit the damage to a business’ network and data. Immediate investigation action is then taken by analysts to triage the incident and respond immediately.
What does this mean in practise?
When the appropriate rulesets and automation are implemented to detect anomalous account activity, rogue processes or malware, the account is temporarily disabled, or the endpoint is temporarily isolated from the network.
The SOC analysts are immediately alerted to a high priority incident which is then triaged as being a true or false positive. If it does happen to be a false positive, the account is re-enabled, or the device is released from isolation. If it’s a true positive the next steps in the response process are then activated.
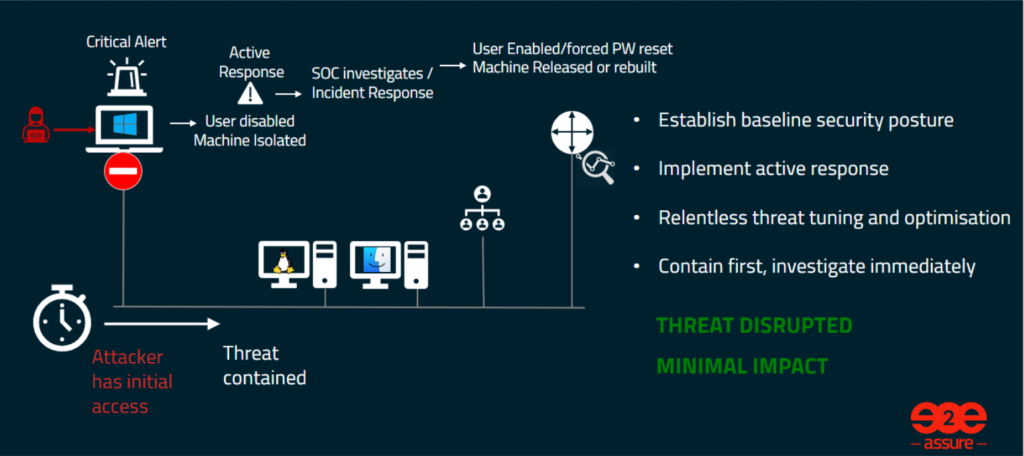
Resulting in attackers being disrupted much further left of the Kill Chain or MITRE ATT&CK frameworks and massively reducing the impact to the business.
The concerns of Attack Disruption
The big concerns and questions that get raised by new clients when we discuss our approach to Attack Disruption is how to minimise the business impact of false positives disabling users and isolating machines?
To address this, we of course have a continual drive for tuning and optimisation of detection rules. But a key process for us is to onboard as much historical log data as possible into our SOC platform, run our analytics over the historical data and observe which alerts would have triggered automatic Attack Disruption actions. Then we tune retrospectively before going live with that assertive automation.
Why is this so important in 2024?
Immediate response actions are vital in 2024 to reduce cyber risk and impact. Data is currency and businesses holding data are seen as valuable targets to threat actors. At the risk of sounding like we’re spreading FUD (Fear, Uncertainty and Doubt, it’s important to remember that proactive and pre-emptive measures are always a better cause of action than reactive.
With over 10 years of Threat Detection and Response expertise, we can assure you that by the time you’re aware of a cyber incident via traditional SOC methods, it’s too late. If you’re interested in finding out more about our Attack Disruption techniques or you’d like to see this in action yourself through on of our demos; contact our sales team today.
