Hacking Android devices
As an active member of the security community, e2e-assure is committed to keeping up-to-the-minute with information security tools, techniques and discoveries. However, we know that the only way the ‘Good Guys’ stay ahead of the ‘Bad Guys’ is by thinking offensively, and beating them to the punch. One way we do this is through security research and vulnerability disclosures to major companies.
The following two vulnerabilities in Android have been disclosed to Google. They have subsequently been fixed, and patches issued to all Android device manufacturers. So what are these vulnerabilities?
Invisible Wi-Fi Monitoring (CVE-2016-2457):
How would you feel if you heard that someone could set up invisible monitoring on all your internet browsing on your smartphone in less than 1 minute, and while your phone was locked? Sounds like something from a spy movie? Nope, this is a real-life Android vulnerability.
Here is an overview of the attack: If the device owner has previously activated Guest Mode the option to switch to this is available in the Notification Panel. When the device is on the lock screen (and PIN/password/pattern locked) an attacker with physical access to the device could switch to Guest Mode and change the 'Advanced' WiFi settings for a currently-connected network, changing the HTTP proxy settings to redirect all the wireless traffic from the Android device through a device in the control of the attacker. The attacker could then log out – locking the screen again – and the owner would be none-the-wiser. There is no indication to the user that his/her settings have been changed. The device would then use these new proxy settings to redirect all the user’s web browsing through the computer the attacker had provided the details of. This computer could capture usernames and passwords, or other unencrypted data; or it could even change the content of pages the user browsed to – automatically injecting malicious code to steal more personal data, injecting malware, or prompting the user to install hacked apps.
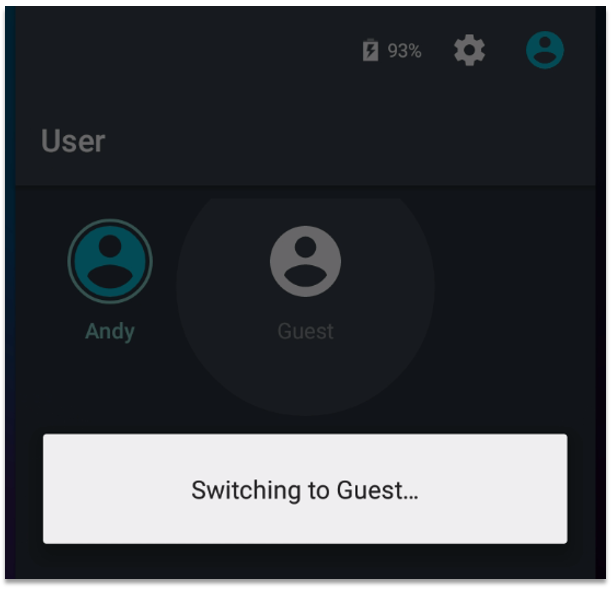
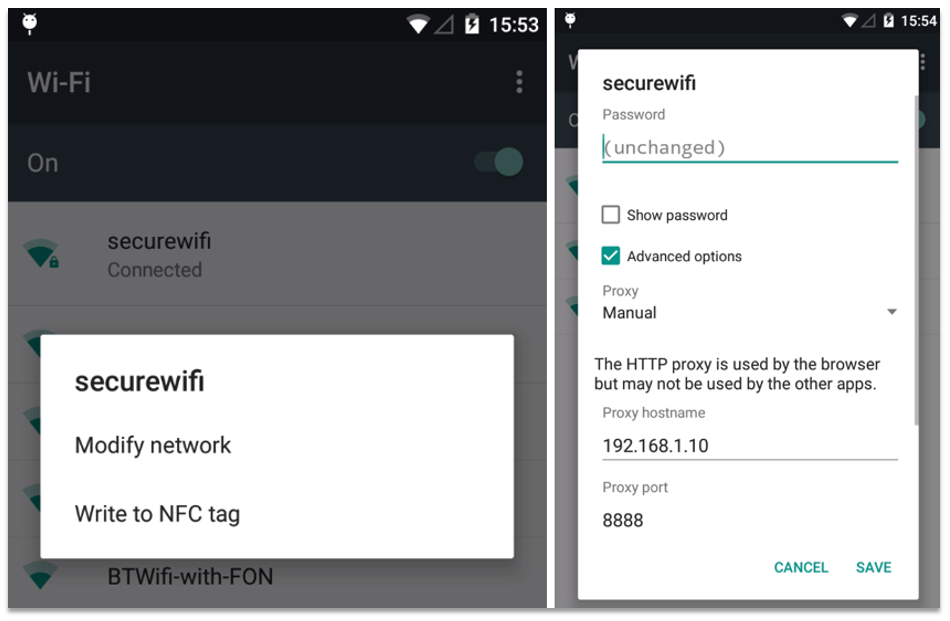
Ghost Bluetooth devices (CVE-2016-3760):
While we’re at it, the attacker has another option open to them: Bluetooth. Bluetooth is well locked-down on Android – you cannot connect a new device without typing in the authorisation code at the time of first connecting. This is because authenticated Bluetooth devices can do a lot on a device they are connected to.
The process of authenticating a device is usually only open to a logged in user: you turn Bluetooth on and select the device you want to connect to. There is often a prompt for a user code to be entered. Once done the device is 'paired' and can communicate in whatever way the device is set up to do.
Some of the functions of Bluetooth devices are: File transfer Keyboard Mouse Audio in (microphone) Audio out (speaker) Custom device (connected to specific apps and able to send/receive data freely)
This attack is performed using the same methods: An attacker with physical access can switch to Guest Mode (if this feature is activated). From here the attacker can access the Bluetooth settings and connect any Bluetooth device. After pairing normally this authorisation will persist for the main device user. Any time the user is in range of the paired Bluetooth device it will connect automatically – allowing it access to the device. From here the attacker could send keystrokes (if using a Bluetooth keyboard) to navigate the file system, access webpages, or send messages. Using HID-injection attacks (HID means "Human Interface Device", i.e. mouse, keyboard, etc.") this can be automated and performed swiftly by a script on the attacker's machine. Alternatively the attacker may connect a Bluetooth headset and receive calls meant for the device owner – perhaps impersonating them, or collecting a 2-Factor token meant for the user.
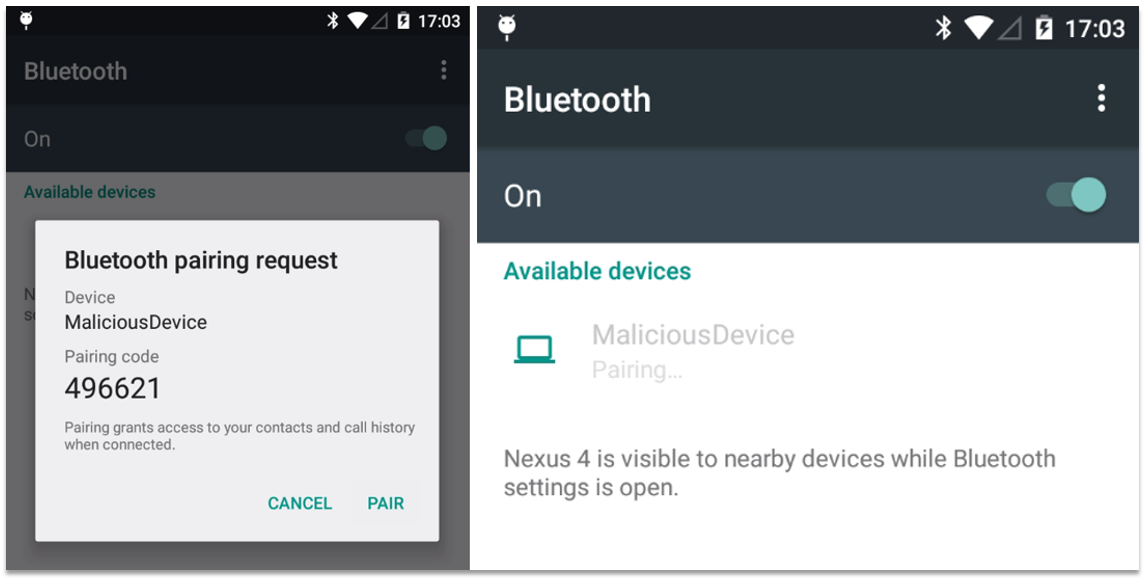
Fixed by Google
Google, to their credit have recognised the implications of these attacks and fixed the issues via Android Security updates. The Wi-Fi issue was assigned CVE-2016-2457 and was fixed in the May 2nd 2016 Security Update. The Bluetooth issue was assigned CVE-2016-3760 and was fixed in the July 5th 2016 Security Update.
However, note that while Google have patched the issues not all vendors push out all security patches to all devices. If you are on Android 6.0 or higher you can check your patch level under 'About Phone' (or 'About Tablet') in the Settings menu. Other devices may or may not enable you to check this.
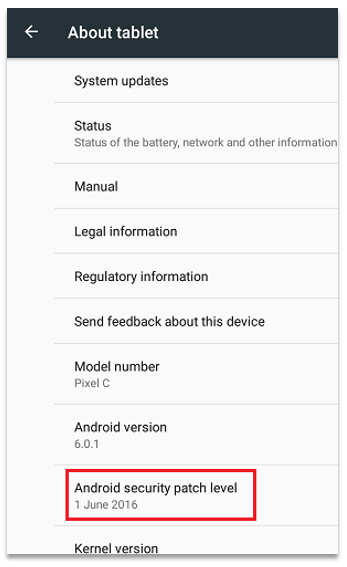
As not all devices have received (or will ever receive) these updates e2e-assure recommends that you disable Guest Mode on your device if you are not using it. Also, bear in mind that Guest mode is more secure than lending your 'logged-in' device to another person, however having physical access to a device – even in Guest Mode – can allow access to more data than you might expect. This is especially the case if your phone is not fully patched and on the latest version of Android.
"Hold on, aren't these 'attacks' just normal features?"
Both of these reported issues are ‘elevation of privilege’ attacks, whereby a limited-access user can gain higher access privileges than the Operating System intended. This is possible due to missing (or misconfigured) security controls on the Guest account. With the release of Android 5.0 (Lollipop), Google added Guest Mode as a security feature to allow users to share their device with other people, without affecting their own privacy. The Guest account has limited permissions – you can’t make calls, or access the data or settings for the main user account. Google describes Guest Mode as a security enhancement – a “mode that can be used to provide easy temporary access to your device without granting access to your data and apps.” (http://source.android.com/security/enhancements/enhancements50.html) This makes it clear that allowing a Guest Mode user to modify settings on the main user's account would be breaking this security context.
Our continuing research…
e2e-assure will continue to research security issues in this and other platforms, reporting these to the parties involved, and keeping your devices more secure in the process.
