Android Photo Vault app analysis (Part 1)
Security is an important issue to all of us today, and we are all realising the value of our personal data. Images in particular are deemed to be important – we have a desire to protect these over most other types of data. And to address that need comes the ‘Photo Locker’ category of apps.
Whether we want to keep corporate secrets in images safe, protect photos of ourselves from others with access to our devices, or keep a personal collection of pictures to ourselves, there are these apps available to keep them safe.
But how much protection do these apps really provide?
That was a question I was keen to answer, after happening upon weak security in a few different types of apps recently.
So I set out with a clean device, and a bunch of top-ranking Photo Vault apps.
Here was what I found…
Spoiler: lots of apps were really bad! See the Findings section below for more details.
Methodology
Firstly, to set the scene, here was the process I followed:
I wiped and Factory-reset an LG Nexus 4, running Android 5.1.1
I also rooted the device, to give access to protected areas of the operating system otherwise unseen to standard users. This would help me test the locations apps were storing data, and also see what some other apps installed on a normal device may be able to access. As we shall see, root access was rarely necessary… but we will get to that shortly!
I installed a file browser – Total Commander in this case, but many others would yield the same results – as stock Android does not have one (although some OEMs do include one by default).
I also installed a packet capture tool on the device (TSharkCapture), although I usually used HTTP proxying through a Windows 10 laptop on the same network, running the excellent Fiddler (from Telerik) to capture traffic.
The only other tools needed were a text-editor and a hex editor (Notepad++ and HxD for preference).
The apps
I determined the apps to test by the complex process of searching the Google Play store for “photo vault” and choosing the top 12 results.
Due to Google’s search algorithms these happened to be the top-ranking or most-installed apps, racking up hundreds of thousands of installs between them.
The list is as below:
- NQ Vault (com.netqin.ps)
- Hide Something (com.colure.app.privacygallery)
- Secure Gallery (com.sp.smartgallery.free)
- Hideitpro (Audio) (com.hideitpro)
- Private Photo Vault (com.enchantedcloud.photovault)
- KeepSafe (com.kii.safe)
- HidePhoto (com.domobile.hidephoto)
- KyCalc (it.ideasolutions.kyms)
- Lock Photos (com.vdg.lockphotos)
- Password Photo Phone Folder (com.passwordphonephotofolder.photolocker)
- Gallery Lock (com.morrison.gallerylocklite)
- Vaulty (com.theronrogers.vaultyfree)
Testing
I installed and ran each of the apps under normal conditions, following the application instructions and guidance as it appeared onscreen.
I created accounts as instructed, and set PINs and passwords as the app required.
The PINs were set to 1234 and the passwords to testing – for consistency.
Each app was tested by encrypting/securing a single image – a screenshot of the Google Play Store page for the app – this also helped identify the app where the file was moved to an obfuscated directory.
As the apps are clearly meant to offer protection against someone who has access to the device, (who would normally be able to view images via the gallery app) I have tested these as the logged in user – attempting to gain access to the images without knowing the credentials provided by the user who secured them.
Theoretically this should not be possible if the apps are doing their job.
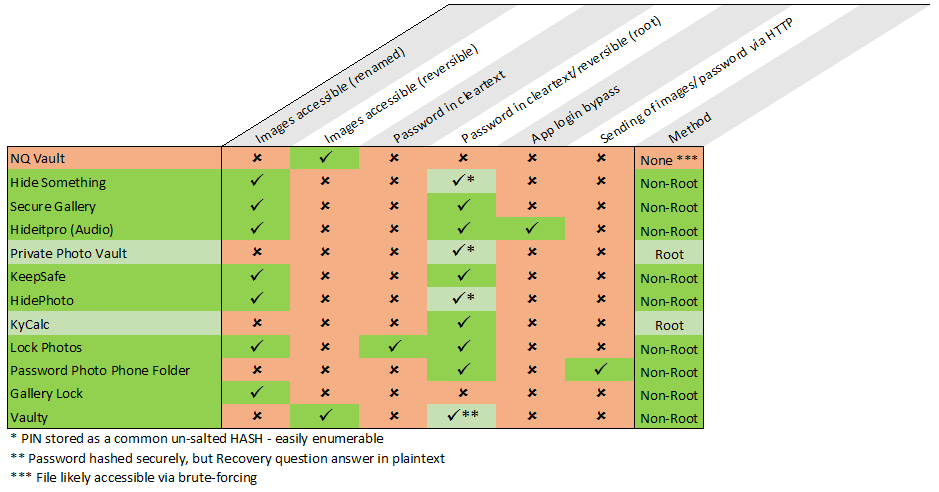
Findings in brief
I have to be honest – I was expecting a mixture of good and bad security practices. This cynicism comes from working in the security industry, and seeing bad practice on a daily basis.
The best practice would be that the apps encrypt the images individually, and move them to a protected area of the file system, or to place them in an encrypted container in a protected area of the file system.
In practice it would appear that very few of these apps followed that process.
Indeed – most of them didn’t encrypt the images at all!!
In many cases the protection of the PIN/password was applied to the app itself, rather than the images. That is to say, you need to use the credentials to open the app, which is where the developers assumed you would access the images. However, in these cases the images were just moved to another area of the accessible file system – somewhere that can be accessed by a file browser (or even the internet browser, if push comes to shove). In many of these cases the images were either just left as they were, or simply renamed to a different file format. A simple rename in the file browser exposed the images.
Out of the 12 apps tested – this was the practice found in SEVEN of these!
Just to reiterate – in nearly two thirds of these apps the images were neither encrypted NOR stored in a protected location, and could be viewed in a file browser.
Aside from this, there were other flaws found in these weak apps, and across the entire test sample.
These ranged from obfuscation of the image files (very different from encryption), to storing passwords in accessible locations, and even sending the images off the device without using any form of encryption in transit.
Summary
In short out of the 12 apps tested I was able to access the images stored in 9 cases just by having physical logged-in access to the device, with the remaining 3 being susceptible to attacks applied via root access.
It is worth noting that some of the root access attacks could have been performed by other apps on the device with overly generous permissions, or from rogue apps or malware. Clearly these are not the usual vectors the apps are protecting against, but we’re all about security in depth – protect things as many ways possible, so if one protection fails, you are still safe.
Below is a chart breaking down the various flaws found in the apps tested.
There will be a series of follow-up blog posts going into some more detail about the flaws found here, as well as giving step-by-step walk-throughs of just how easy it was to extract the images from these ‘photo vaults’.
And if that wasn’t enough we will give you some useful tips about how to use the inbuilt protections in Android, or some secure solutions to keep your images and other data safe.
Keep your eyes on the blog.
Footnote
All of the app developers were contacted several times in the month or so prior to the publication of the blog.
e2e-assure follows a Responsible Disclosure process and always warns developers before publicly reporting any security risks in apps/websites etc.
None of the developers acknowledged the reported issues, or were willing to comment on the security of their apps, or whether they would be patching the reported issues.
It is however interesting to note that a couple of them have disclaimers on their websites regarding the security of their apps. These shy away from any protections afforded by the apps being foolproof, with one even going as far as to say:
As with any mobile application with limited functions, [app name redacted] does not protect your mobile device or image and video files against third party unauthorized access.