Top Attacks Against M365

M365 (Microsoft 365) is a cloud-powered productivity platform used by nearly half million companies in the UK. With 4 out of every 5 fortune 500 companies using M365, it’s safe to say that this is a very popular tool for many organisation.
However, this high level of popularity plays into its downfall. With many companies, of all sizes, utilising the platforms solutions M365 is a great starting point for attackers to attempt to gain access to a companies data, IP or infrastructure.
Why do attackers focus on M365?
Attackers don’t focus solely on M365, they use multiple tactics across many platforms to attempt to gain access into companies networks. But the widespread popularity of M365 makes it a typical target as this is where businesses may store important data or IP via SharePoint Online and OneDrive on Office apps such as Excel and Word; conduct day-to-day corporate communications via Teams and send documents and email requests via Outlook.
The most common attack types
The most common attacks on M365 accounts are:
- Phishing
- Business Email Compromise (BEC)
- Email Account Takeover
- Cloud Data Theft
- Ransomware
- Data Theft
Many sources quote phishing as the most common attack. Phishing is what’s known as an ‘Initial Access’ method that can then lead to a successful compromise. The attack could be targeting data (data theft), trying to steal a user’s account (identity theft), or focused on deploying ransomware (ransomware attack) – in some cases, it could involve all three.
How these attacks take place
Please keep in mind, the better the M365 licence you have, the more security solutions and tools will be available to you. Even with the SMB licenses like Microsoft 365 Business, you can achieve great results by reducing your attack surface and greatly improving your security posture, particularly when every licence can also be upgraded and customised using add-ons from Microsoft and allowing flexibility to incorporate additional security features as and when organisations need them.
Your basic M365 user will use Azure Active Directory (AAD) to authenticate access to M365. If this user account is compromised, then the attacker has access to all the data and applications that are available to the user, across all the platforms.
M365 users will typically store lots of sensitive information in their email (Outlook) as well as OneDrive/SharePoint and OneNote. If an attacker can login as the compromised user, it’s very easy for them to steal data and start causing serious disruption and typically, the organisation will be completely unaware. The attacker may use this initial access to penetrate further into the organisation, as once in it’s easier to move laterally. Attackers may also decide to sell this access to other criminal cyber groups that may have other motives and deploy further attacks.
Cyber Risk = Likelihood x impact
When considering cyber attacks many organisation want to know what their risk of these attacks might be. Unsurprisingly, the biggest cyber threats also create the greatest cyber-related risk for organisations.
Cyber risk is defined as Likelihood x impact. The impact is often measured against the cost to repair or recover from the attack or by other business metrics such as reputational impact, financial impact, or business continuity capability.
The impact is typically the ‘outcome’ of the attack, including but not limited to financial loss, business disruption, reputational damage, or regulatory penalties. That’s why phishing is number one because it’s the most common and can lead to high impact attacks such as those described above – that’s a big impact!
Real world scenarios: The impact of M365 attacks
Let’s consider a few scenarios:
- Phishing leading to M365 account takeover –>
Account takeover leading to fraudulent invoices through the use of email, to deceive suppliers and customers.
Resulting in: financial loss, reputational damage
Likelihood: HIGH
Impact: HIGH/MEDIUM - Phishing leading to M365 account takeover –>
Account takeover leading to data theft, the ransom of that data
Resulting in: Fines, more financial loss and legal costs & reputational damage
Likelihood: HIGH
Impact: HIGH - Phishing leading to M365 account takeover –>
Account takeover leading to theft or destruction of IP, or other critical data.
Resulting in: Business failure, loss of competitive advantage & loss of investment
Likelihood: HIGH
Impact: HIGH - Phishing leading to ransomware –>
Ransomware leading to data theft, the ransom of that data and potential destruction of that data.
Resulting in: Fines, more financial loss and legal costs, reputational & infrastructure damage.
Likelihood: HIGH
Impact: HIGH - Phishing leading to malware being deployed with the organisation –>
Malware passed on to the supply chain, leading to business being the source of supply chain compromise of other organisations.
Resulting in: Complex legal problems, business disruption, loss of customers, etc.
Likelihood: HIGH
Impact: HIGH - Phishing leading to M365 account takeover –>
Account takeover leading to supply chain attack. The attacker uses stolen accounts, and access to other companies. Businesses typically targeted here are MSPs or similar that use their Azure AD accounts to access other organisations to provide helpdesk and support services.
Resulting in: Complex legal problems, business disruption, customer loss, etc
Likelihood: HIGH
Impact: HIGH
How to keep your M365 account protected
As we’ve demonstrated, there are multiple ways phishing can lead to high impact attacks. M365 is a fantastic productivity and modern workplace tool but you need to ensure you have firstly, properly secured it and secondly, that you have the means to detect and respond to attacks quickly.
Speed is vital here as catching those successful identity attacks before the attacks move on (before the actual data theft or before the ransomware is deployed) is essential. This is often referred to as ‘disrupting the attacker kill chain’ or ‘shifting left’ – this means stopping the attack early and is an essential element of cyber resilience.
The graphic below shows a typical timeline for a ransomware attack and illustrates the importance of detecting and responding to attacks as early as possible.
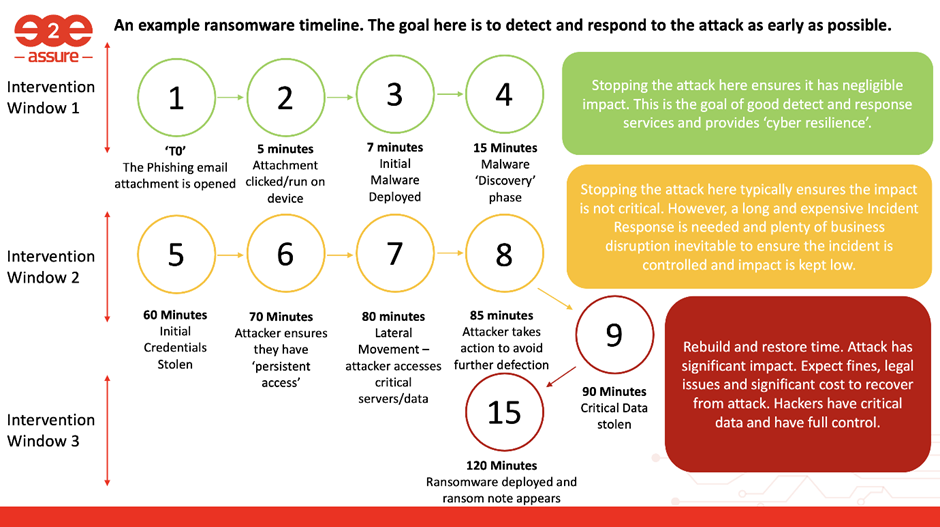
How do you achieve this?
The advice is this – secure M365 and monitor it.
You can view our Top 10 Tips for Securing Your M365 account to make this process easier. Be ready to detect and stop attacks before they can cause harm/impact. Be ready to disable user accounts quickly and take other similar actions such as quarantining files and disconnecting devices from the network. Assume you will suffer a successful attack (this is referred to as ‘Assume Breach’) and plan for it.
Assume Breach generally refers to a cyber strategy where it assumes that the business is either already breached or could easily be. This is seen as an effective, modern strategy to identify and address potential gaps in detection, response and recovery and when implemented effectively gives organisations confidence that they are cyber resilient, which is the key goal of cyber security strategies.
Through effective security monitoring, attacks can be detected and responded to in the same way as other business issues – expect them to happen and put measures in place to address them quickly and effectively. Detections and responses to attacks need to be practiced and rehearsed; this is why you see a lot of advice around ’table-top exercises’ and so forth; because the first place to start is by planning for the worst and using that exercise to get your organisation ready for that inevitable, successful attack.
Your goal is to minimise impact by stopping the attack before it has a high impact (‘shifting left’). This is how you will achieve cyber resilience which is essential for your business. Only then can you effectively manage your cyber risk.
Rob Demain, CEO
Follow Rob on LinkedIn.
