Maktub Locker – An overview
Ransomware has unfortunately been gaining in popularity over the last year.
With targets such as hospitals and schools 'paying up' to get their files decrypted, ransomware has become the latest menace to both home and corporate users.
When we spotted a download page for Maktub (a new strain of ransomware), we decided take a look at just what it was like to have a machine infected. We started with a Windows 7 virtual machine in our lab, and went to the download page we had spotted…
Stage 1: The Hook
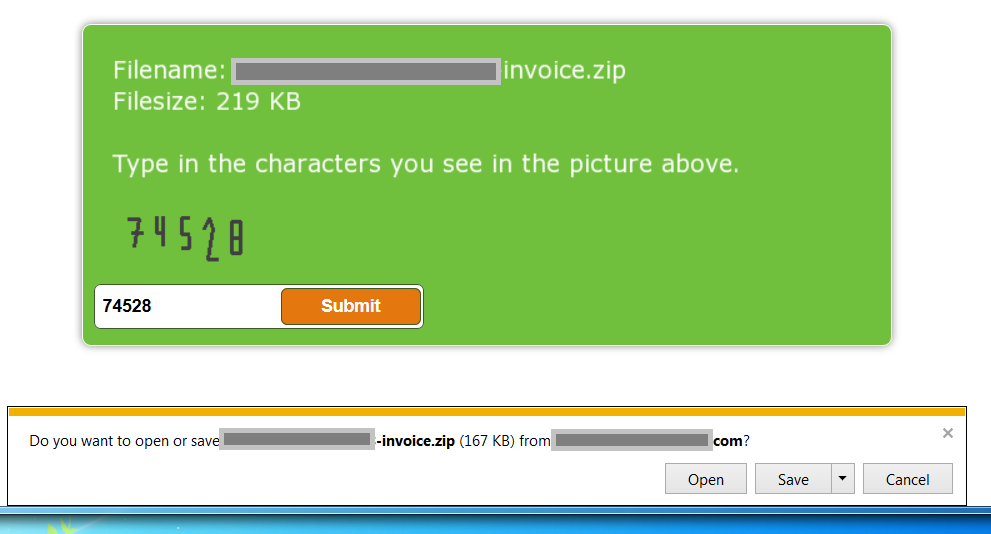
In most cases, a link to a Maktub delivery page comes in a phishing email. Here, we found it on a compromised website – where the compromised page was made to look like a download form. The page even has a box to enter a captcha code! The file to be downloaded is a suitably intriguing 'invoice' type document
After entering the verification code, we downloaded the file onto our test machine
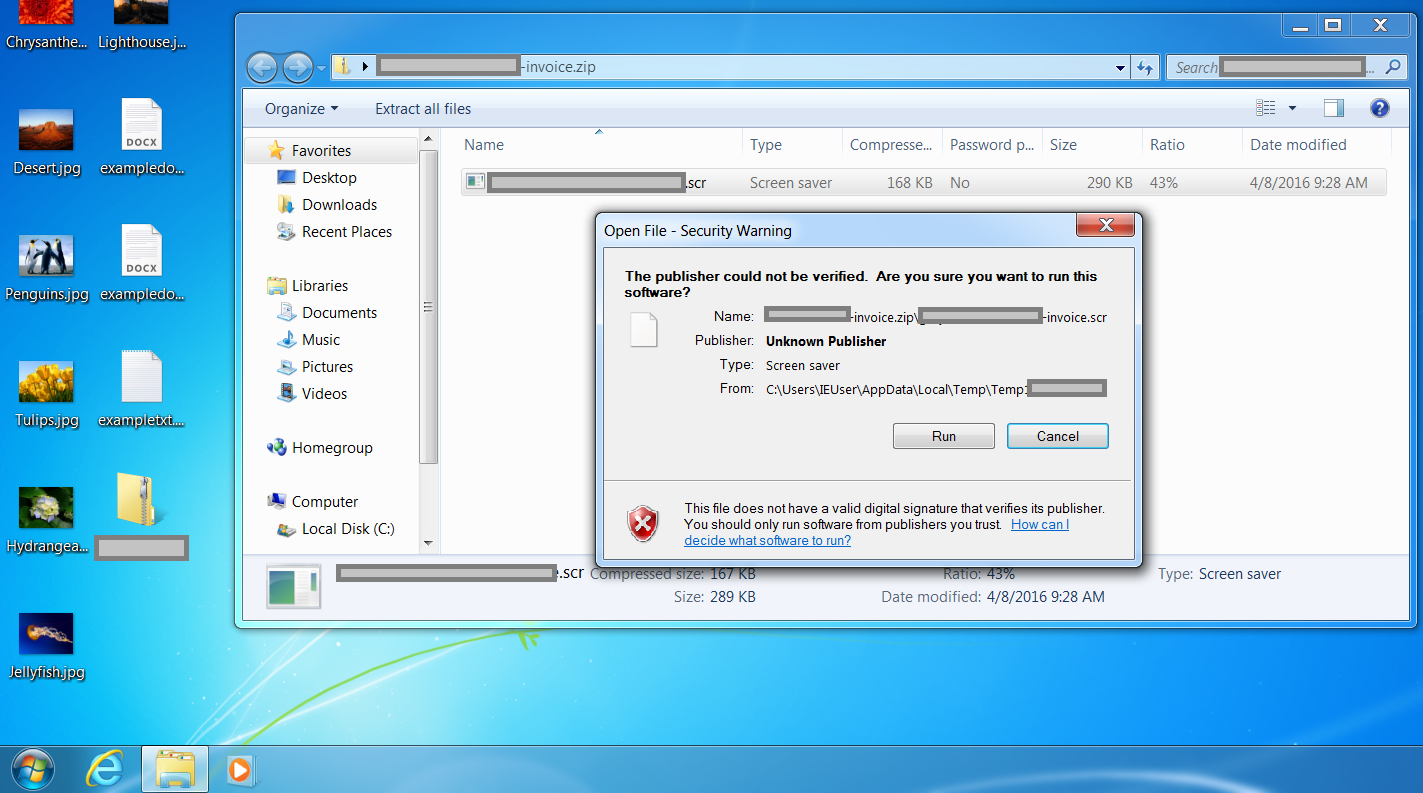
Stage 2: The Line
We unzipped and opened the file – which, we can see from the security warning, presents itself as a .xls file (but with a .scr extension – an executable). Strange for an invoice! Here, we see that user interaction and confirmation actually is needed to open this file
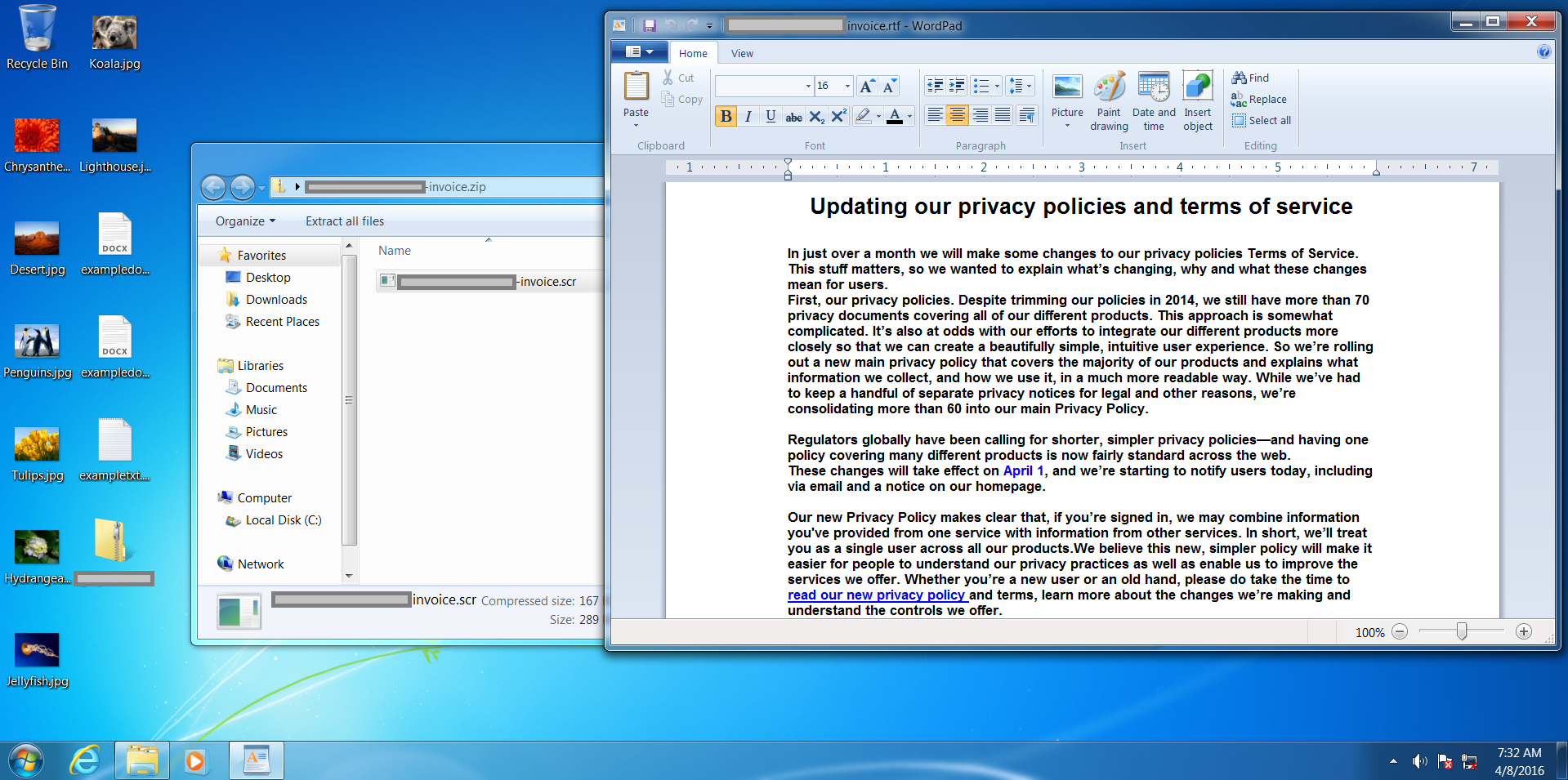
We are shown a .rtf file now – even stranger! Some 'privacy policy' text is shown – designed to distract the user whilst files are encrypted in the background
Stage 3: The Sinker
After about 30 seconds, a pop-up window is shown for 'Maktub Locker'. Also notice that our files have disappeared from the desktop!
Interesting about Maktub is that it relies heavily on 'brand recognition' – presenting the user a heavily stylised 'ransom note' which they will probably recognise as being ransomware! After going to the (user personalised) link, a demand for payment will be shown, to be made in Bitcoins, usually around £300-500 per computer.
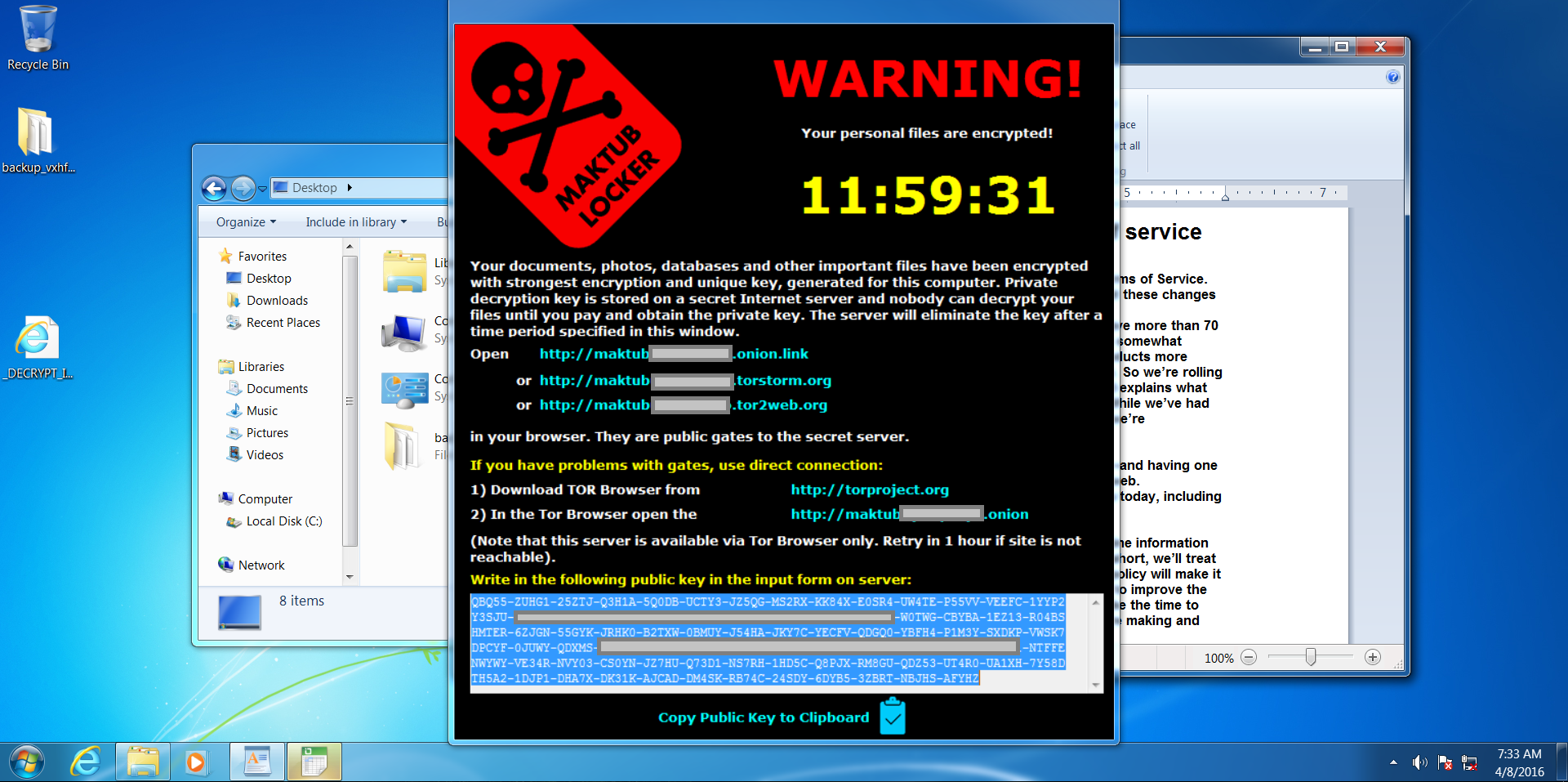
Here we see our files have been encrypted and renamed – we can't get into them or make sense of them at all!
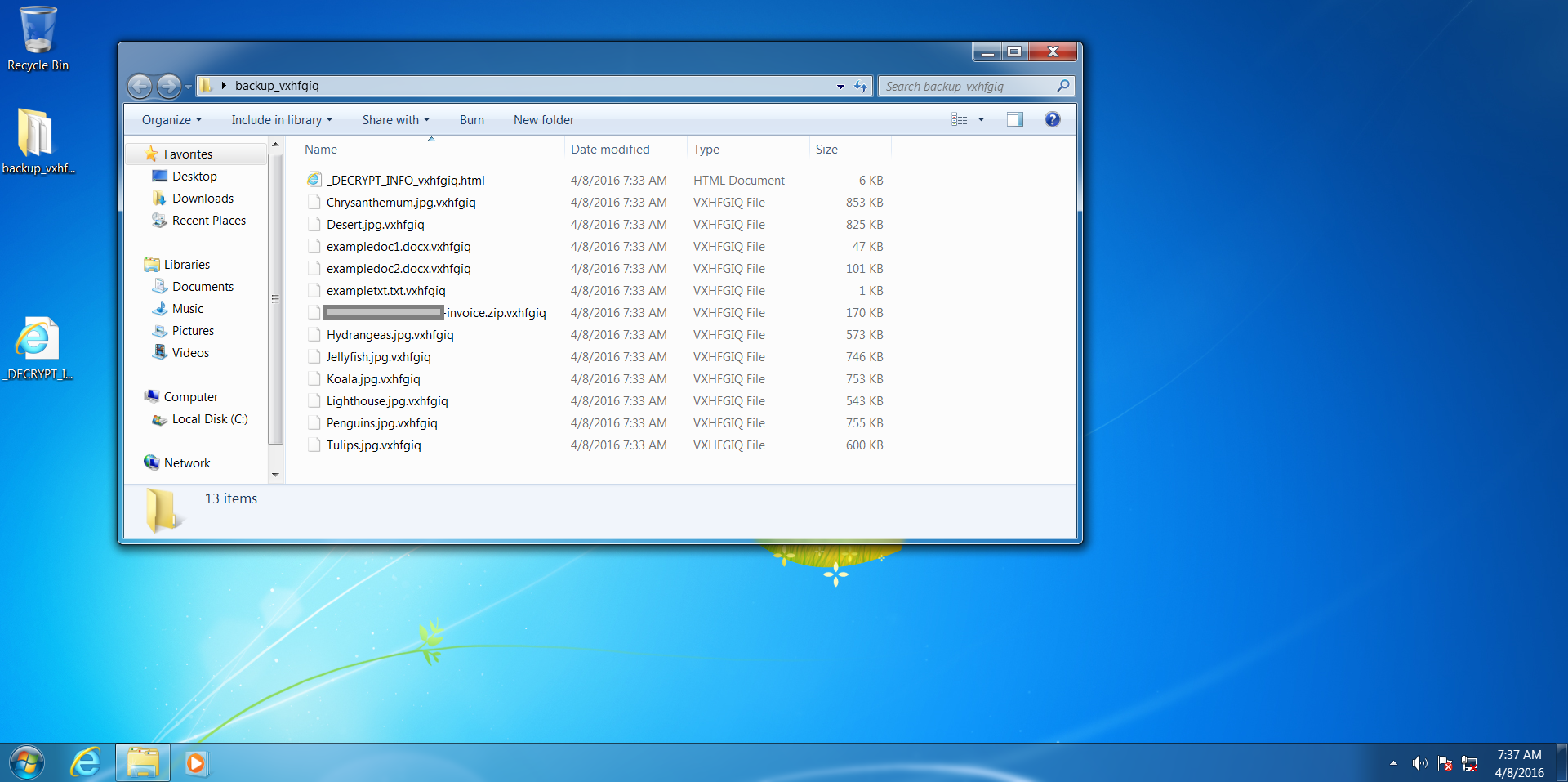
After clicking on the personalised link, we were shown an even more heavily stylised explanation and demand for payment – with a price list. The introduction page even sounds apologetic! But don't be fooled, behind these well-designed pages is a ruthless business model, and to prove this a Bitcoin address to send the ransom is listed on the last page
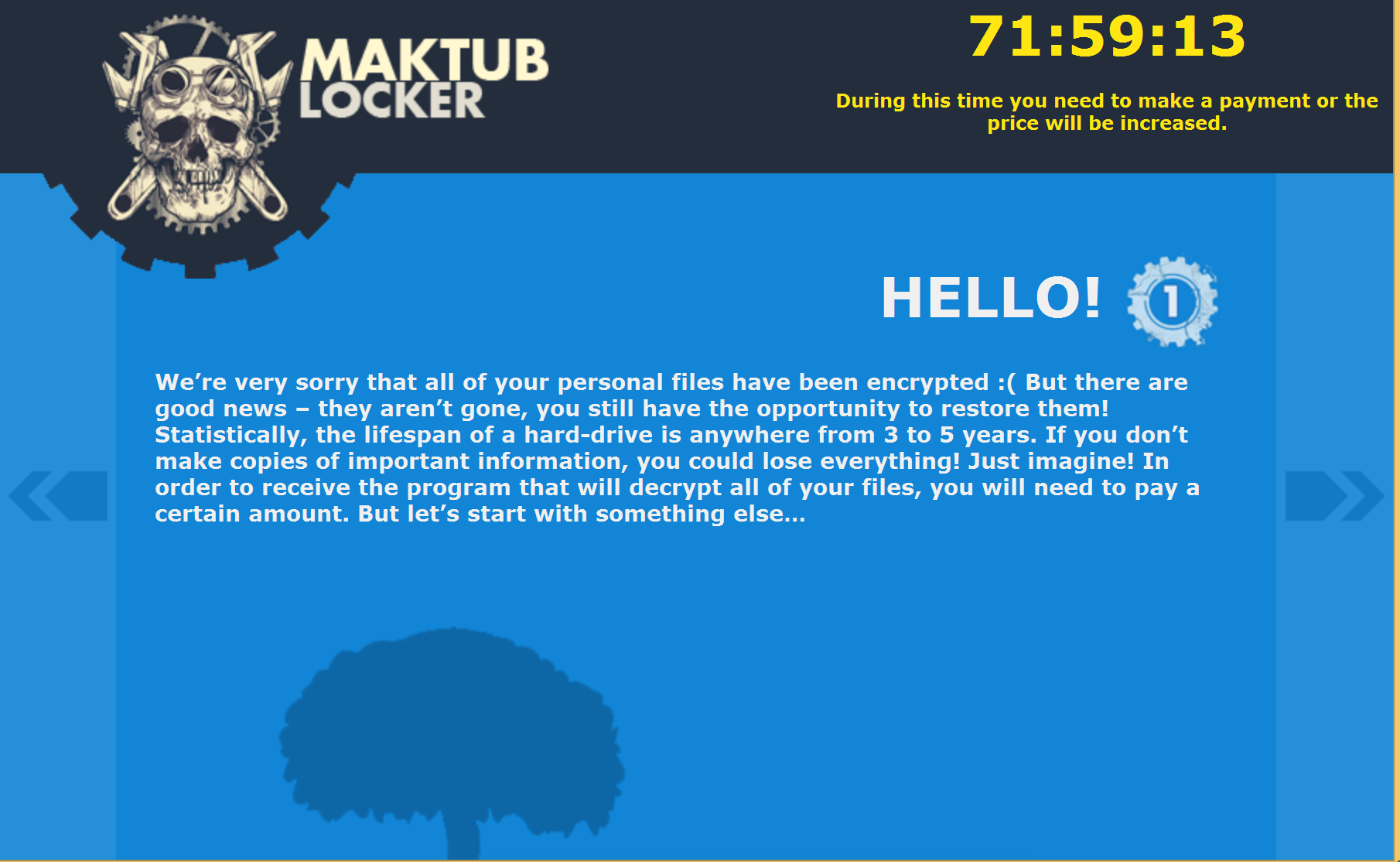
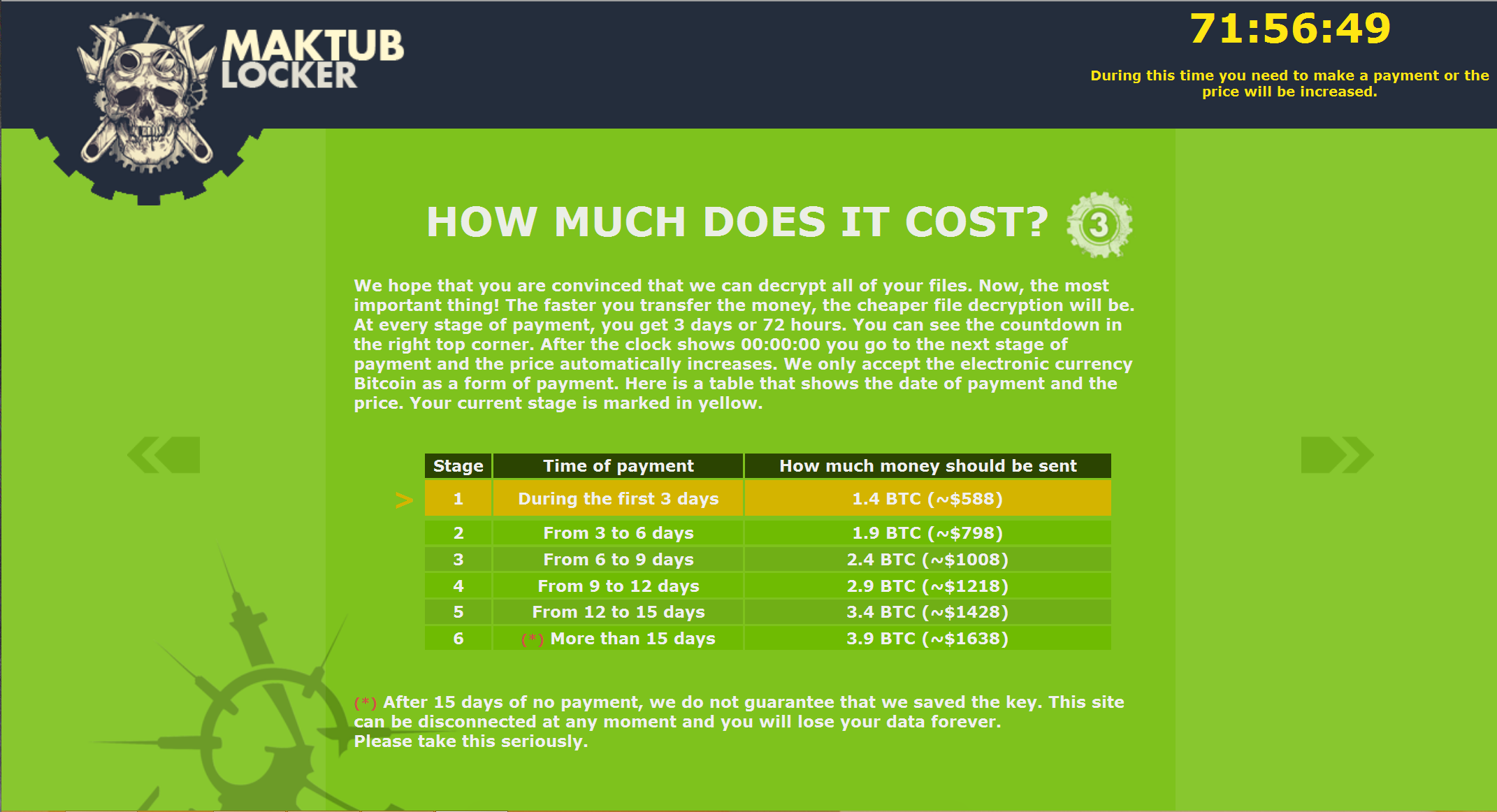
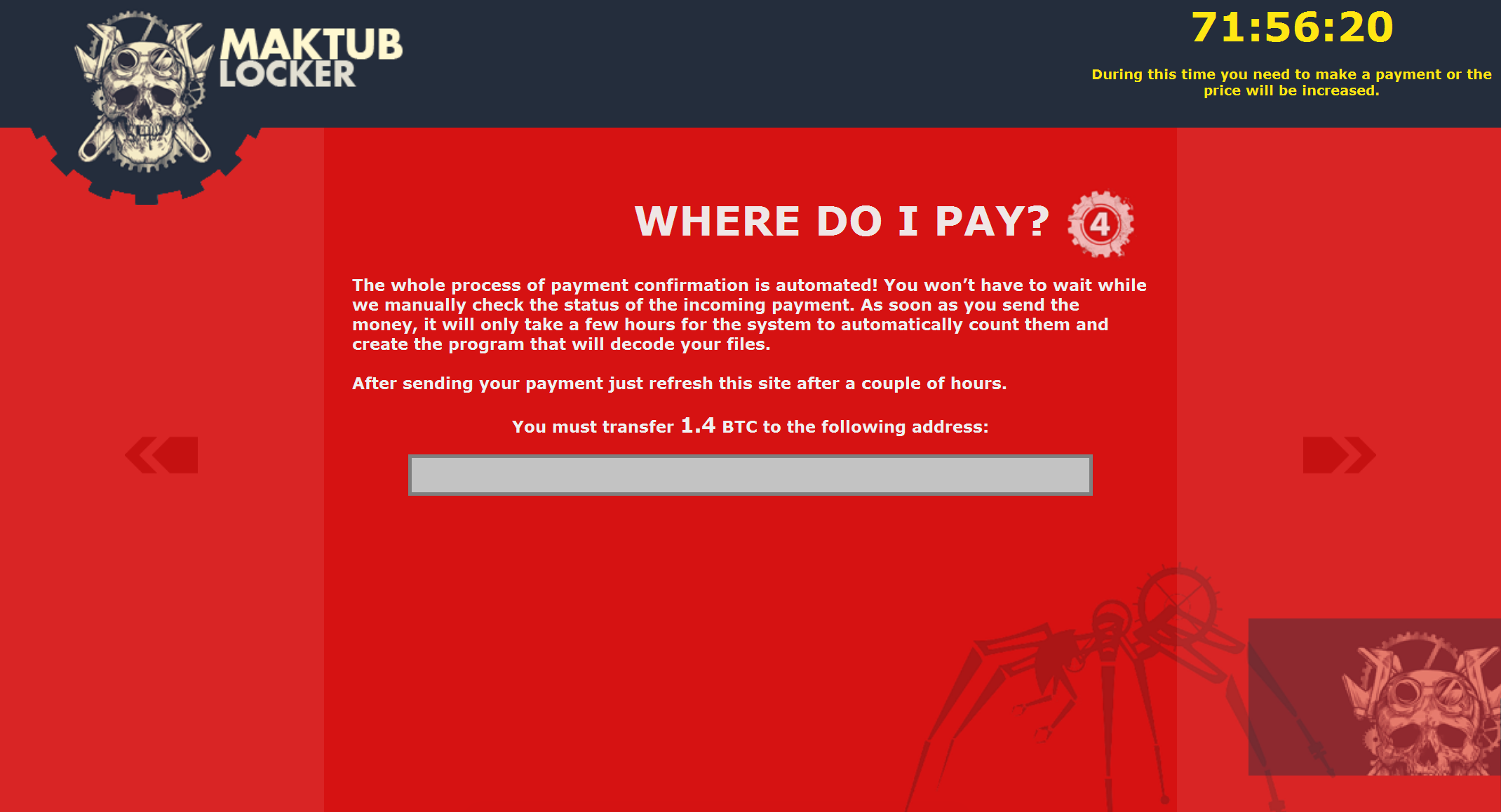
Protecting against Maktub Locker
Don't get caught short on your backups!
The single most important thing to mitigate the damage done by ransomware is to have off-line backups. Multiple backups are even better. Having backups means that instead of paying a ransom, the infected system can be wiped and files then restored. Again, MAKE GOOD BACKUPS. This is the single most important thing to undo the damage done.
Do not pay the ransom
Paying a ransom does three things:
- It funds the cyber-criminals who are behind the ransomware. Not only does it make them richer, it can also help fund other kinds of more serious criminal activity, and provides an incentive to continue
- It provides more funds for the continued development of ransomware. It gets smarter and harder for the 'good guys' to detect and protect against
- It helps persuade companies that paying the ransom is a viable 'way out' of the situation. It often isn't, and there is no guarantee that files will be decrypted. And, bad news, cyber-criminals do not offer 'money-back' guarantees!
Educate your users
Here, we also saw the actions a user has to take to infect the machine with malware. We had to click through two separate warnings! Educate users about not downloading or opening suspicious files. This also applies to files by email – especially unexpected ones with attachments (commonly 'invoices', 'remittance advice', 'fines' and 'CV's. Often, users are just trying to 'get the job done' and may let this override their sense of suspicion. Make sure users know that it is okay to take a slower, more secure approach (not opening suspicious files) – even if it might mean a missed deadline!
Run system updates
Most ransomware uses well-known vulnerabilities in software to compromise systems. Keeping systems up-to-date limits the chances of ransomware even being able to run.
Get help
If you do get hit, don't be afraid to reach out to the technical community. For some well-known ransomware variants, there are free decrypting tools available to recover files without paying a ransom.
Report it!
If you get hit, report this to ActionFraud (or the NCSC if you're an organisation) as this will help them track the spread of this type of crime.
Conclusion
Again, make backups! Ideally, there should be multiple backups, including 'offline' backups which cannot be reached by a computer without being physically 'plugged in'. These mean that the ransomware cannot find and spread to the backup location.
Unfortunately ransomware is going to keep growing in popularity with the criminal world as a way of making money. However, the good news is that there are ways of preventing infection or minimising the damage done.
