‘Angler’ Exploit Kit – web-based JavaScript malware

When e2e-assure discovered a suspicious webpage had been visited by a host on a client’s network we decided to analyse the script contained within the webpage to find out its functionality. What we discovered was a landing page used by the sophisticated exploit kit ‘Angler’…
This blog post details the process of de-obfuscation and analysis carried out against a copy of a malicious webpage in order to reveal the intent of the script lurking within it.
Analysing the malicious page
The HTML Code
The html code for the page in question had several interesting features:
- English-language text from Jane Austen’s ‘Sense and Sensibility’ inserted into seemingly random HTML elements tags
- Paragraphs of encrypted text
- A highly obfuscated JavaScript section
It was determined that whilst the English-language text served a purpose (making the page look slightly more legitimate), it did not contribute to the page’s functionality and was removed for clarity during the analysis. Attention now turned to the obfuscated JavaScript. Without altering the underlying code, the JavaScript was tidied-up by removing white space and formatting the syntax to be more easily readable:
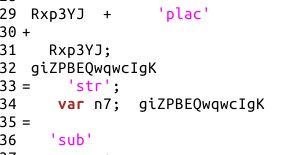
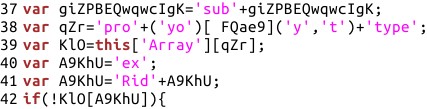
After de-obfuscation, the purpose of the script was made much clearer and comments were added to the script as the analysis progressed:
The JavaScript
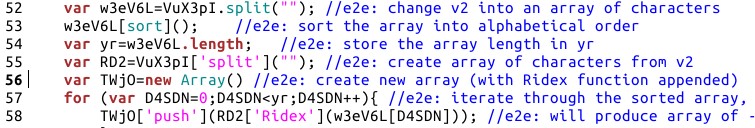
Next, all superfluous sections of JavaScript (acting as decoys) were removed and function calls were renamed to express inherent functionality, and the file was ‘tidied-up’ once more. This showed the JavaScript had three main sections:
- An apparently unused function at the top of the section
- A ‘core section’ with the purpose of decrypting the encrypted text paragraphs in the document body, which then used the ‘appendChild’ method to add them to the main document
- An array, containing encrypted unknown data
Within the core decoding section the ‘appendChild’ call was replaced with a function to show the encrypted paragraphs from the document body decrytped into a plain text in a ‘textarea’ tag. The decoded JavaScript functionality was thereby displayed, and through analysis of this code the following was determined about it : - It contained a file-checking function, which checked for common anti-virus programs installed on the system
- It checked for a Kaspersky virtual keyboard (raising suspicions the final payload might include a key logger program– a virtual keyboard might interfere with the function of a key logger program)
- It created and opened an Adobe Flash Player object, delivering a presumably corrupted movie file from a known malware site
The Investigation
After this decryption was complete it was possible to search online for distinctive lines from the JavaScript, and a reference was found to this exploit on the FireEye blog, containing further explanation of the stages of payload deployment for this exploit kit (including Diffie-Hellman key exchanges and the downloading of shellcode)
This ‘Angler’ exploit kit was attempting to use a vulnerability (patched in July 2015) which is documented on Microsoft TechNet
The webpage accessed by a user of our services contained code used by the ‘Angler’ exploit kit. This kit has been previously used to deliver payloads such as the Cryptowall ransomware – a nasty piece of malware detailed on BleepingComputer
Once again, this illustrates the importance of keeping operating systems up-to-date and patched. The witnessed attempts to legitimise and hide the functionality of this landing page shows clear intent by the developer to circumvent traditional signature-based intrusion prevention and endpoint protection controls.
Preventing infection from Exploit Kits
There are a number of basic steps that can be taken to help prevent Exploit Kits like Angler from introducing malware into your network:
Keep operating systems and applications up-to-date
Exploit Kits target software vulnerabilities. Keep operating systems and key applications like Flash, Java and browsers up-to-date. There are a number of applications commercially available that complement OS vendors’ own update systems to deploy third-party software updates including Flash, Java etc. and report on non-compliant systems.
Only use privileged accounts where necessary
It is recommended to use privileged accounts for system administration tasks only and use a separate, lower-privilege account for day-to-day tasks. Malware will commonly run with the privilege-level of the currently-logged-on user. If that user has administrative privileges, the malware has unrestricted access to key areas of the system to establish persistence and spread through a network – especially important when dealing with ransomware.
Ensure Endpoint Protection and Intrusion Prevention controls include web-based protection functionality and are configured to receive regular signature updates
Exploit Kit landing pages have unique signatures and can be detected by anti-malware and anti-intrusion controls that are aware of these signatures. Landing pages are becoming more sophisticated in their obfuscation, but client-based intrusion prevention and endpoint protection modules can still prevent exploitation before the payload is downloaded, providing web-based detection is active and up-to-date.
